Table of contents
- 1. Configuration Guide
- 1.1. Start VPN Server Manager
- 1.2. How to enable and configure IPsec with vpncmd
- 1.3. How does a L2TP/IPsec VPN user have to specify his username to login? (with Standard Password Authentication)
- 1.4. How does a L2TP/IPsec VPN user have to specify his username to login? (with RADIUS OR NT Domain Authentication)
- 1.5. User Authentication with L2TP/IPsec VPN Function
- 1.6. Configuration for EtherIP / L2TPv3
- 1.7. Note
- 2. IP Address Assignment for L2TP Logged-in Users
- 3. How to Traverse a NAT / Firewall?
- 4. See Also
The IPsec VPN Server Function is disabled by default. You can enable it easily as the following steps.
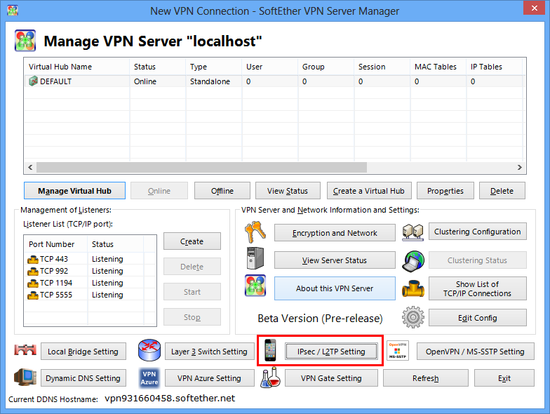
Configuration Guide
Start VPN Server Manager
The meanings of each option are followings:
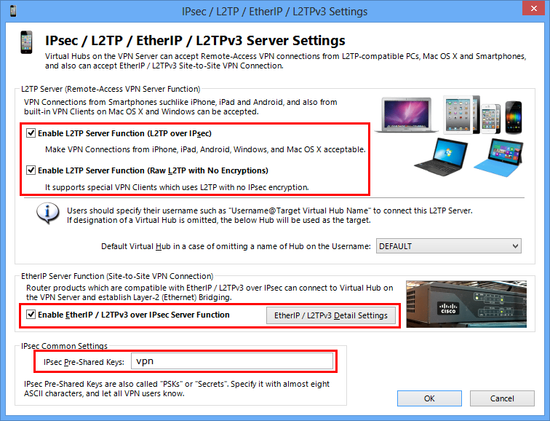
- L2TP Server Function (L2TP over IPsec)
This function is for accepting VPN connections from iPhone, iPad, Android, and other smartphones, and built-in L2TP/IPsec VPN Client on Windows or Mac OS X. Enable it if you want to support one of these devices as VPN Client.
- L2TP Server Function (Raw L2TP with No Encryption)
Some special-configured VPN router or client devices have only just a L2TP protocol without IPsec encryption. To support such a strange device, you have to enable it.
- EtherIP / L2TPv3 over IPsec Server Function
If you want to build site-to-site VPN connection (Layer-2 Ethernet remote-bridging), enable EtherIP / L2TPv3 over IPsec. You have to add your edge-side device definition on the list.
- IPsec Pre-Shared Key
IPsec Pre-Shared Key is sometimes be called "PSK" or "Secret" . This string is "vpn" by default. However, changing it is recommended. You have to inform the latest key to all VPN users.
How to enable and configure IPsec with vpncmd
If you cannot use VPN Server Manager GUI for Windows, alternatively you can use vpncmd to activate and configure the IPsec VPN Server Function, by the IPSecEnable command. To learn how to do it in vpncmd, run "IPsecEnable ?" command in the vpncmd prompt.
How does a L2TP/IPsec VPN user have to specify his username to login? (with Standard Password Authentication)
How does a L2TP/IPsec VPN user have to specify his username to login? (with RADIUS OR NT Domain Authentication)
User Authentication with L2TP/IPsec VPN Function
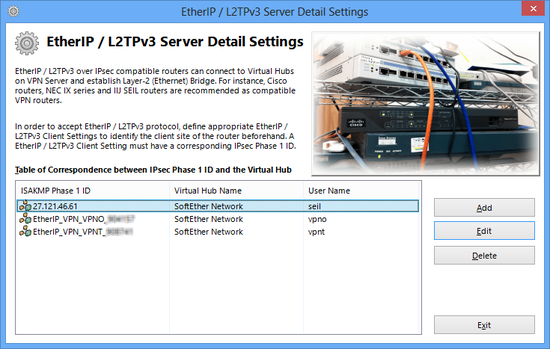
Configuration for EtherIP / L2TPv3
EtherIP and L2TPv3 is for accepting VPN routers to build site-to-site VPNs. You can click the "EtherIP / L2TPv3 Detail Settings" button on the configuration screen to add the client-device entry on the list. On a client-device entry on the list, the ISAKMP (IKE) Phase 1 ID string, and the related credentials (username and password on a user which has been registered on the destination Virtual Hub.)
You can specify the asterisk ('*') as the wildcard on the username on an entry. Such an entry will be applied for any VPN client router's login attempts from remote side.
EtherIP / L2TPv3 Server Detail Settings
Note
IP Address Assignment for L2TP Logged-in Users
In L2TP function, an IP address of a VPN Client must be assigned automatically by a DHCP server on the destination Virtual Hub's segment.
Therefore, you have to at least one running DHCP server on the destination L2 segment which the L2TP VPN Client attempts to login.
An IP address will be leased from the DHCP server, and the IP address will be assigned on the L2TP VPN client session. Default gateway, subnet mask, DNS address and WINS address will be also applied on the L2TP VPN client. So if no DHCP server, no login successes.
You can use any DHCP Server which is already existing on your local network. You can use SecureNAT's Virtual DHCP Server Function which is implemented on SoftEther VPN Server if you don't any DHCP servers on the LAN.
How to Traverse a NAT / Firewall?
If your SoftEther VPN Server is behind the NAT or firewall, you have to expose the UDP port 500 and 4500. On the NAT, UDP 500 and 4500 should be transferred to the VPN Server. If any packet filters or firewalls are existing, open UDP 500 and 4500 ports.